The Demise of LOCKBIT: Disrupting the Most Prominent Ransomware Gang by Utilizing Upstream Threat Intelligence
The success story illustrates the power of proactive threat intelligence in a coordinated fight against cybercrime.
Introduction
LOCKBIT is widely recognized as a prominent example of the criminal business model known as “Ransomware-As-A-Service” (RaaS) and its dangerous consequences. In 2021, we started our initial investigation into LOCKBIT’s campaigns which eventually led to in-depth insight into all of their 28 affiliates and facilitated the decryption for hundreds of victims. However, in the last years, the group’s influence, operational scope, tactics, techniques, and procedures (TTPs) have significantly evolved, impacting thousands of organizations globally.
Since LOCKBIT’s first entry into the cybercrime ecosystem, PRODAFT has diligently assisted NCA, FBI and other partners of Operation Cronos to better understand and disrupt this criminal enterprise.
This success story aims to shed light on the achievements and challenges faced by our Threat Intelligence Team over the past four years while researching one of the most formidable cybercrime syndicates that has ever existed worldwide.
Challenges Faced by Our Threat Intelligence Team
During our investigations, PRODAFT needed to overcome a variety of challenges coming hand in hand with the concerningly aggressive actions of the LOCKBIT threat group:
- Prevalence of Ransomware-as-a-Service (RaaS): Despite the existence of RaaS before LOCKBIT, it emerged as a pivotal example of this business model and its dangerous potential to generate illicit financial profits. The utilization of LOCKBIT’s locker software by hundreds of sophisticated threat actor groups (affiliates) under a unified brand significantly hardened attributing specific TTPs to the group.
- Diverse Client Infrastructures: As an experienced Threat Intelligence provider, we at PRODAFT aim to offer applicable mediums, playbooks, and scenarios to our clients. However, the broad spectrum of TTPs employed by LOCKBIT’s affiliate network against various sectors presented a major challenge in devising effective, tailored solutions for each client's profile.
- Scarcity of Actionable Intelligence: Despite ongoing publications by threat intelligence firms and public authorities on LOCKBIT, this publicly available knowledge often lacked specific, directly actionable intelligence on an affiliate- or product-related basis.
- Reactive Intelligence Exchange Methodologies: Traditionally, victims and security solution providers only became aware of new TTPs after an organization had been compromised and undergone a detailed digital forensics/incident response procedure. This reactive approach delayed understanding the latest “state of the art” tactics that had been used during the compromise.

What Started as a Cybersecurity Concern Turned Into a Notorious Ransomware Powerhouse
The PRODAFT Threat Intelligence Team was first alerted to LOCKBIT following a general request from a large Swiss law firm through our CTI platform in early 2021. The initial investigation ignited a deep interest in the somewhat intricate inner workings of the ransomware gang. Subsequently, it provided essential insights into LOCKBIT's internal structures (at that time known as LOCKBIT 1), revealing the entire kill chain, operational management, recruitment practices, and financial flows.
The investigations carried out by our Threat Intelligence Team pinpointed over 28 LOCKBIT affiliates and successfully obtained all decryption keys for their ongoing campaigns. These pivotal discoveries significantly accelerated the overall identification of the largest network, ultimately leading to the disruption of this criminal enterprise. Thanks to continuous information-sharing with law enforcement agencies, hundreds of companies that were originally targeted by LOCKBIT were supported in their decryption efforts. It's noteworthy to mention that within the course of three years, the number of LOCKBIT affiliates had increased to 194, according to the information provided to PRODAFT by the U.K. National Crime Agency (NCA).
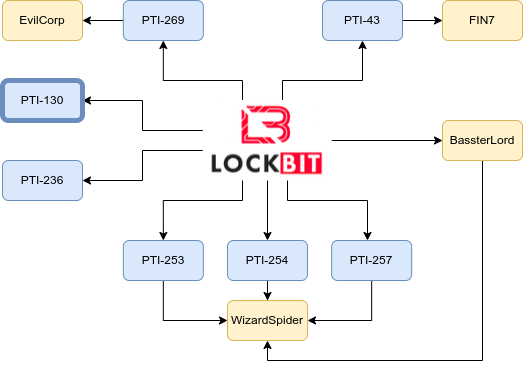
Subsequent investigations focused on the unique TTPs of each LOCKBIT affiliate, leading us to the mapping of multiple groups of affiliates as shown in Figure 1 (PTI-269, PTI-43, PTI-130, PTI-236, PTI-253, PTI-254 and PTI-257). This extensive mapping and analysis enabled the PRODAFT team to gain in-depth visibility into each affiliate’s structures, including ties with other notorious groups such as FIN7, Wizard Spider, and EvilCorp.
During the course of our research, PRODAFT has diligently shared our findings, especially those classified as TLP:RED, with authorized law enforcement agencies, ensuring continuous and careful deconfliction processes were being followed.
Dealing with the Threats LOCKBIT Brought to the Table
Aligned with our mission, PRODAFT’s primary goal has always been to protect citizens, businesses, and governments from major security threats by providing timely and accurate information. Our efforts against LOCKBIT affiliates have focused on delivering up-to-date and actionable intelligence, empowering our clients to preemptively and proactively address next-generation cyber threats. Our key contributions include:
- Mapping out unique TTPs of LOCKBIT affiliates (PTI-269, PTI-43, PTI-130, PTI-236, PTI-253, PTI-254 and PTI-257):
This research enabled us to provide our clients with up-to-date tactical and operational intelligence on each newly created campaign. As an example, the affiliate who focuses almost exclusively on GIT and Jenkins Servers, the affiliate who relies on compromised RDP server information from certain IABs or the affiliate who primarily focuses on vulnerable Fortigate and Citrix platforms have always been on our radar, long before these TTPs have become public. - Obtaining visibility on the affiliates who are in charge of training other affiliates (such as Bassterlord): This visibility enabled us to create proactive threat notifications to ensure that our clients are always prepared and know who are they standing against. We were able to relay the latest firewall evasion and AV bypassing techniques that had been indicated in the training manuals of LOCKBIT affiliates.
- Continuous monitoring of initial access brokers resulting in early warning of all our clients: This monitoring helped us to notify our clients in time, especially in cases when a compromised (and verified) VPN credential of any client had been detected in the infrastructure of an initial access broker (such as WAZAWAKA), who had verified ties with LOCKBIT. (Note: Some of our findings on this particular initial access broker have already been published in our public report dated December 2023.)
- Notifying hundreds of victims at initial access, network discovery or lateral movement stages of their attack: Thanks to these early notifications, the affected parties acquired around 24 to 48 hours of action time before the ransomware was about to be deployed.
All in all, PRODAFT has openly shared its intelligence on affiliates and infrastructures with law enforcement authorities, contributing to ongoing efforts focused at dismantling criminal networks and identifying suspects.
Conclusion
Through our investigations and collaboration with law enforcement agencies, we have successfully shielded our clients and affected parties from LOCKBIT’s detrimental impact. These efforts simultaneously contributed to the timely notifications and early warnings to critical national infrastructures at risk across the globe. Our ongoing investigation into LOCKBIT over the past 4 years presents a significant milestone, deepening our understanding of the Ransomware-as-a-Service model. This example underscores the value of proactive threat intelligence by actively mapping out the adversarial landscape. By focusing on understanding the inner workings of each affiliate’s modus operandi, we keep embedding strategies that have proven essential, over and over again, in the successful fight against the RaaS model and cybercrime in general.

